NPS allows you to create and apply network access policies for the authentication and authorization of connection requests throughout the organization.
Requirements
- Have a functional Active Directory
- Have DHCP and DNS services active.
- Have an MFA application created on the IRONCHIP platform
Implementing NPS on the server
Install the "Network Policy and Access Services" role by adding roles and features.
Create network policy
To create the network policy, open the network policy server, right-click on network policies within the policies tab, and create a new policy.
Give it an identifying name (this name will be used when installing the NPS plugin to determine which policy to protect), and click next.
In this tab, we will select the user group that this policy will apply to.
In the next tab, leave "Access granted" selected.
On the next screen, configure the authentication methods you will use. Click Next.
The next screen is for configuring the restriction to automatically deny access if one of these restrictions is not met. Complete it with the options you want. Click Next.
On the next screen, you can add the configuration that will be applied when the policy restrictions are met. Click Next.
The last screen is a summary of the selected configuration. Verify that everything is correct and click Finish.
You have added the network policy, and everything is ready to create the service and install the NPS plugin.
Plugin
To install the plugin, you need the IRONCHIP Windows NPS file, which can be downloaded from the Add-ons section on the Ironchip Dashboard.
After downloading the plugin, proceed to install it.
Click Next, accept the terms of use on the next screen, and click Next again.
On the next screen, complete it with the following information:
- Your Ironchip host. If you use our cloud solution, it will be api.ironchip.com. Otherwise, provide your custom host.
- Your company's API key obtained when creating the service.
- The name of the network policy you want to protect with Ironchip NPS. In the example, the created policy, IronchipProtected, will be used (if you want to add more than one, put the names separated by a comma and space).
- Then click Next to continue.
Once on the next screen and with all the parameters correctly configured, click Install.
If everything has been correctly configured, and the installation was successful, you will see the following screen. Finally, to complete the installation, click the Finish button.
You also need to create the application in the IRONCHIP panel that references the MFA application.
Finally, add users to that application. (Use the Domain\User name format)
Check its operation
To check if everything is configured correctly and working, we will use a third-party tool, NTRadPing.
Download the application from https://ntradping.apponic.com/
Before entering the application, we will have to create a radius server to perform the test. To do this, open the network policy server, go to RADIUS clients and servers, create a new one by right-clicking on RADIUS clients.
In the panel that opens, you have to enter the following data:
- Identifying name for RADIUS
- IP of the server where it will be installed
- A secret key for RADIUS
Now, if we open NTRadPing and fill in the fields it asks us for (Remember to restart the service to apply the settings).
- IP of your server
- Port it will connect to (default is 1645)
- Time before aborting and how many times it will execute
- User's password
- RADIUS server key
- User to be used
Video tutorial
Installation on Windows Server 2008 and Windows Server 2012
Before proceeding with the installation of the Ironchip Plugins NPS, the following installations and configurations are required:
JDK and .NET (our team will provide these plug-ins), we also need to make a change to the Ironchip certificate format to be accepted.
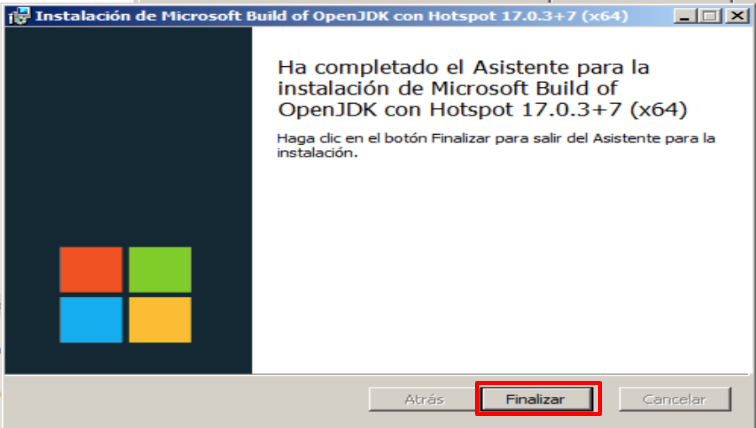
JDK Installation
Open the program and click on Next.
On the next screen, we accept the terms of the contract and click Next again.
In the window that appears below you have the possibility to customise the installation, however, the default configuration is enough for the subsequent installation, so in this case, it would only be necessary to click on Next.
When you get to this screen, just click on Install.
If everything has gone correctly, you will see the following screen and click Finish.
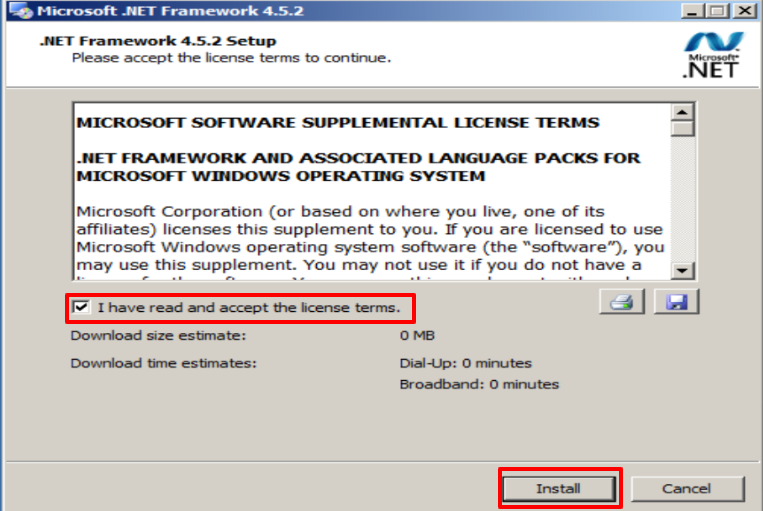
.NET installation
Note: This step is optional on Windows Server 2012.
When you run the program on the next screen, you must accept the terms and conditions and click on Install.
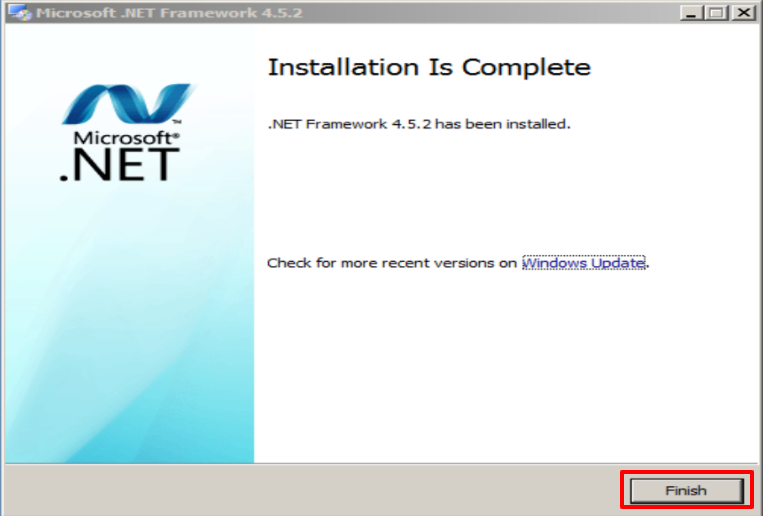
Once the installation is complete, you will find this window and click Finish.
Change of the format of the Ironchip Certificate
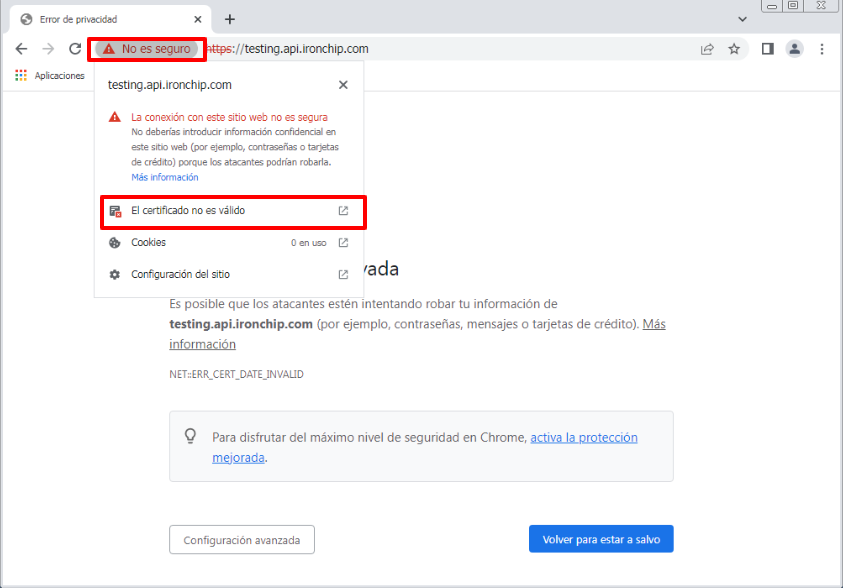
The first thing to do is to enter the api.ironchip.com in your browser (in this case Google Chrome was used), but this can be done from the browser of your choice.
Then in the section where it indicates: “Not secure,” we click and we will see the option “The certificate is not valid”, we click there.
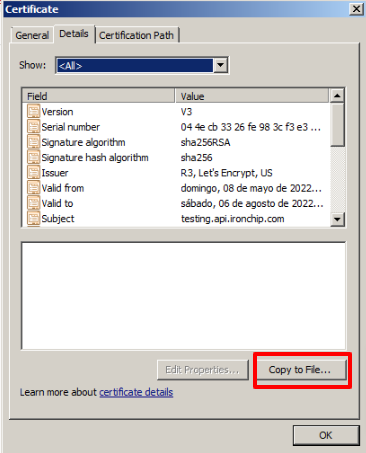
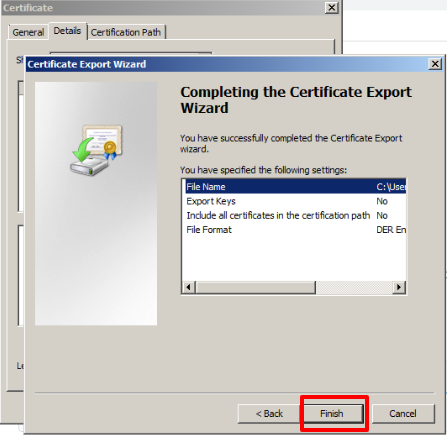
On the next screen go to Details, and click on the Copy to File… option.
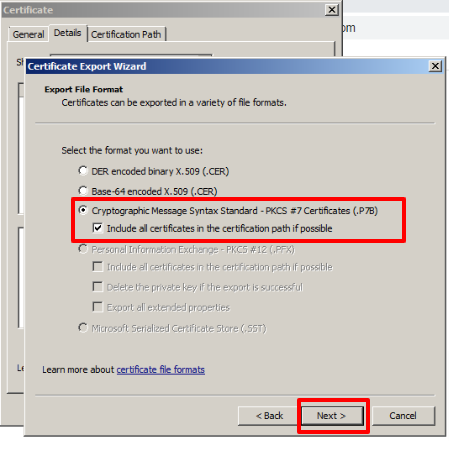
In the next window, we choose the third option and select the checkbox Include all certificates in the chain if possible.
Then click on Next
A new window will open where you click on Next.
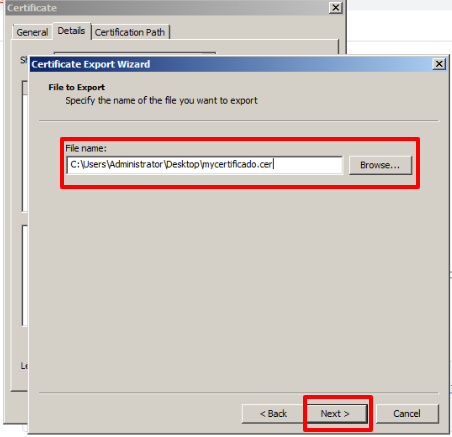
On the next screen, we choose the path where we want to export the certificate and the name we are going to reassign it. Once this process has been carried out, click on Next
The Export process will be carried out and then you will see the following screen and press Finish.
At this point in the process, we already have the certificate in the correct format on our computer, so we proceed to import it.
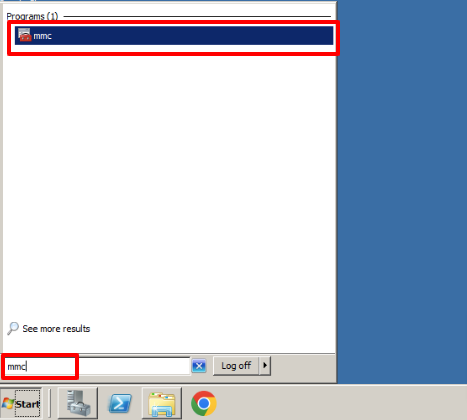
In the program search engine we look for: mmc. Click on the program.
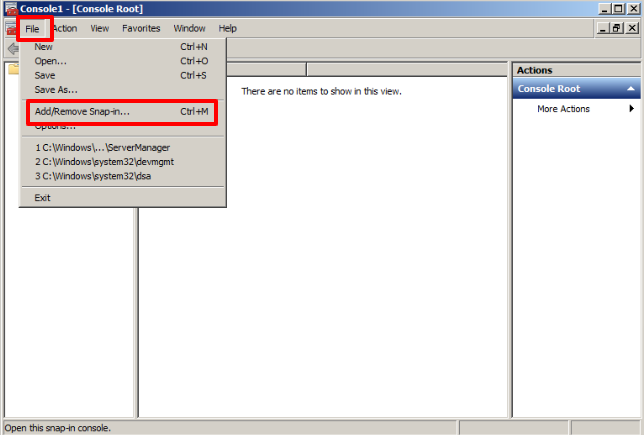
In the next window, we choose File and then Add/Remove Snap-ins
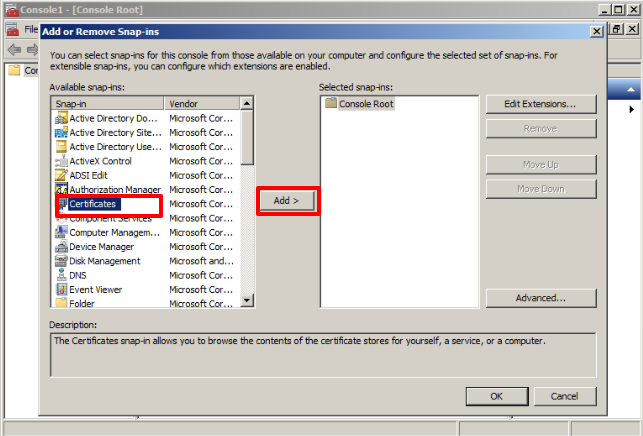
The following window will appear, select Certificates and click on Add.
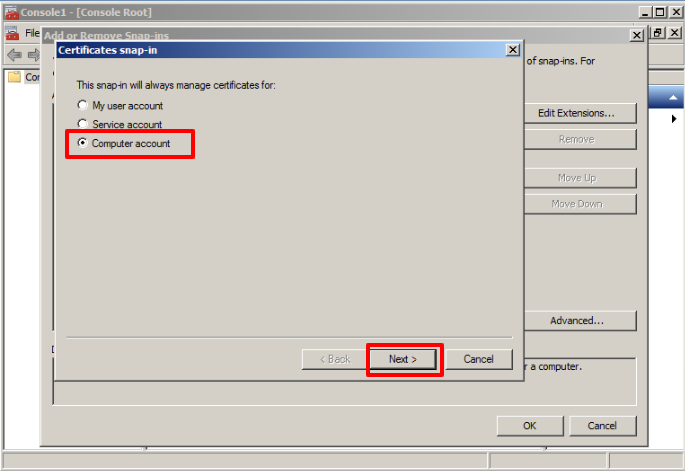
In the next window, choose the Computer account option, click Next
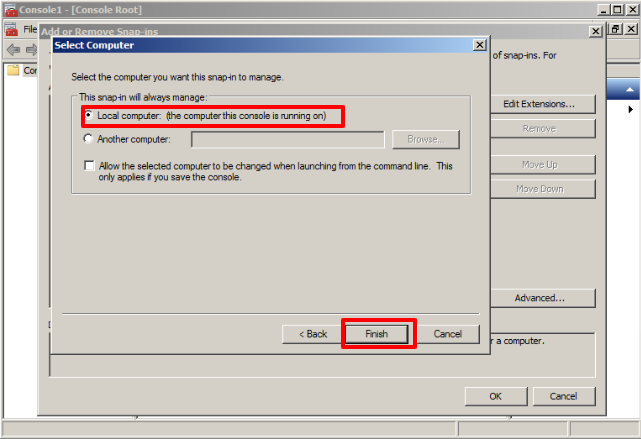
Then choose the first option shown and click on Finish.
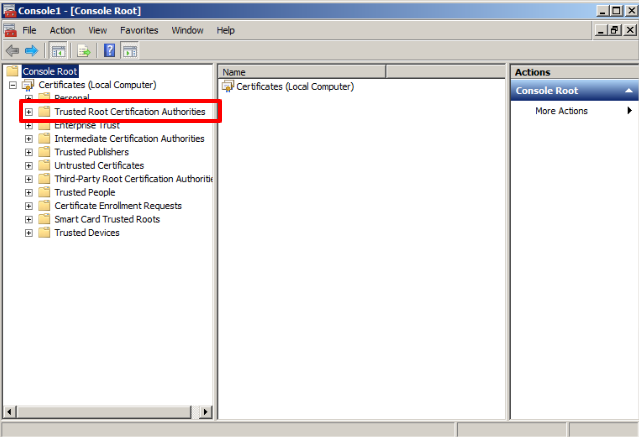
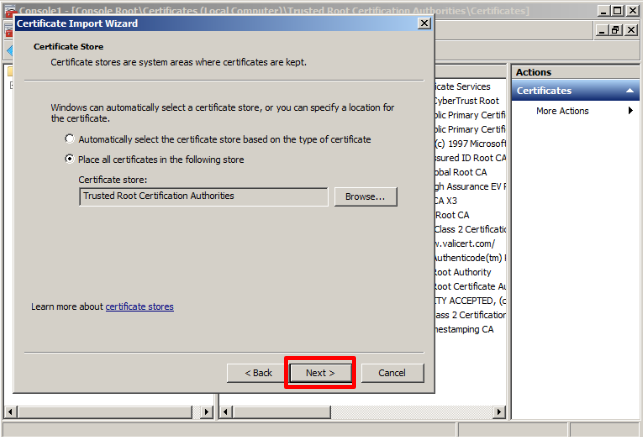
Now in the Console Root folder (local) Certificates will be added, click on them, and the following window will be displayed, there we choose the option Trusted Root Certification Authorities.
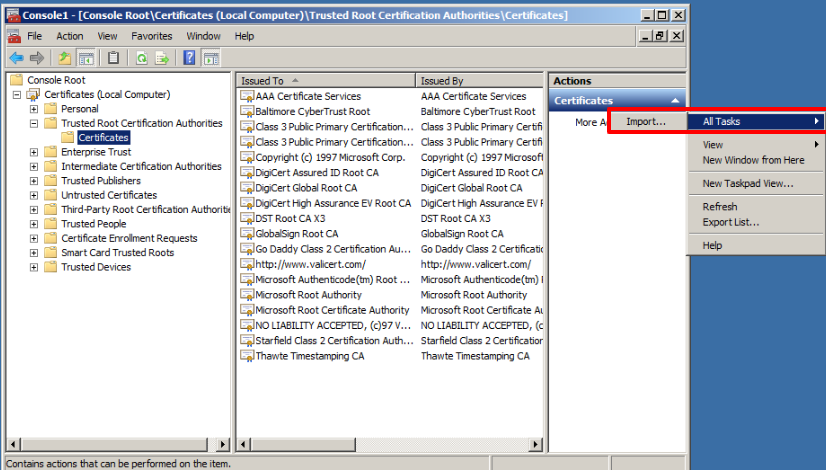
Expand the Certificates folder inside the previous folder and then in the rightmost tab of the screen choose More Actions, then All Tasks, and then Import.
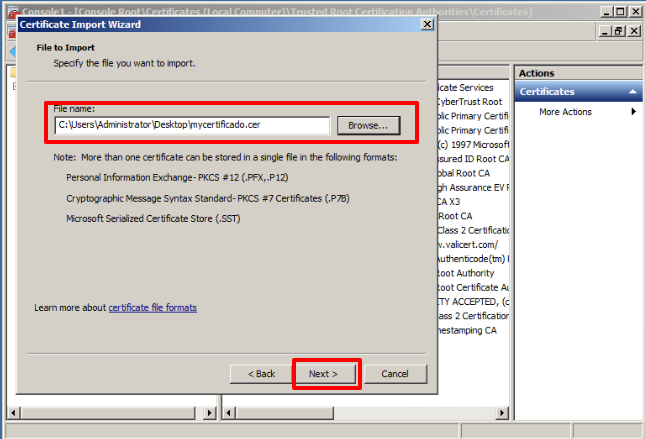
A window will open where we must choose the location where we have previously exported the certificate.
Note: it is important when choosing the certificate to select the correct extension, so it is recommended to choose: AllFiles( * . *).
Then click on the option Next.
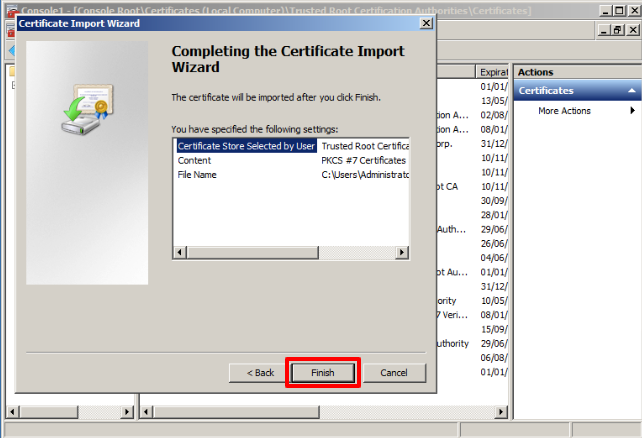
In the next window, click on Next again.
A window with the import summary will be displayed, just click on Finish.
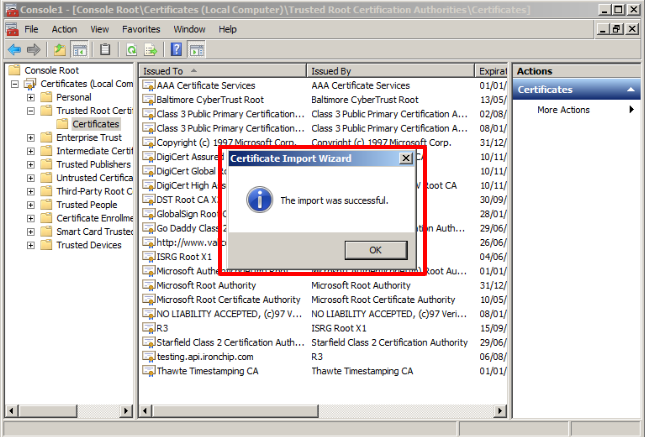
If everything went correctly, the next window will be a Successful Import screen, click OK.
Test NPS Plugin
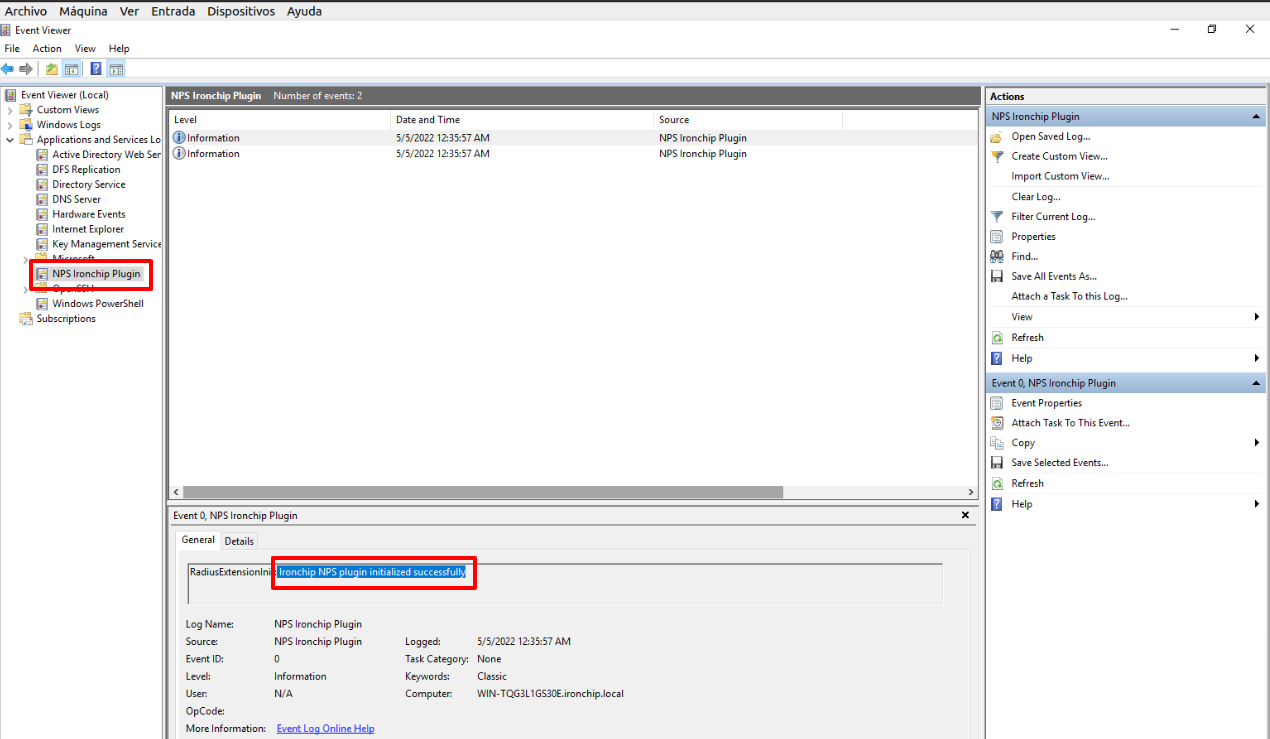
Access the Event Viewer to view the IronChip NPS plugin logs.
If everything is OK, you should see NPSP Ironchip Plugin in the list of applications and services logs. Click on it, and if the plugin is installed you should see Ironchip NPS plugin initialized successfully. in the logs as you can see here:
Note: If you get the message “Unable to load IronChip license key.” Check that it is the correct license and try again. If the problem persists, contact IronChip support for assistance.
Troubleshooting
“User XXX is not authenticated in service XXX. Please, try again.
The user is not authenticated, or authentication has not been valid. Just try again authentication in same page.
“Unable to load IronChip license key. Check that it is the correct license and try again. If problem persist contact IronChip support for help.”
This error means that the license format is not valid. Please, contact info@ironchip.net with the error, and we will validate the license key used and provide a valid one if not valid.
“Event ID 4402: There is no domain controller available for the domain”
You do not need to rename your domain or back rev. You was able to resolve this issue by adding the following reg key to force authentication to use DNS name, instead of the NetBIOS name:
- New string value (REG_SZ): Default Domain.
- Data: example.loc (or example.domain.loc).
“The API-Key provided is not valid. Please, contact IronChip support and send logs for assistance.”
This error means that the license has the correct format, but is old or invalid. Please, contact info@ironchip.net with the error, and we will validate the license key used and provide a valid one if not valid.
“Ironchip has failed. Sorry. Contact support to allow us to solve the problem.”
This error means that some strange thing has happened. If you see this error, contact IronChip support mail, info@ironchip.net, providing error log printed in Event Viewer IronChip MFA logs.






-png-2.png?width=599&height=604&name=Untitled%20(1)-png-2.png)
-png-2.png?width=602&height=607&name=Untitled%20(2)-png-2.png)
-png-2.png?width=602&height=607&name=Untitled%20(3)-png-2.png)
-png-2.png?width=600&height=605&name=Untitled%20(4)-png-2.png)







-png-2.png?width=622&height=683&name=Untitled%20(5)-png-2.png)
-png-2.png?width=597&height=429&name=Untitled%20(6)-png-2.png)

-png.png?width=480&height=612&name=Untitled%20(7)-png.png)
-png-1.png?width=693&height=439&name=Untitled%20(8)-png-1.png)